Deep Diver – Azure AD B2C – Azure Monitor integration, configuration and delegation explained
I wrote this blog because configuring sign-in and audit log export from Azure AD B2C to Azure Monitor based onLue lisää
I wrote this blog because configuring sign-in and audit log export from Azure AD B2C to Azure Monitor based onLue lisää
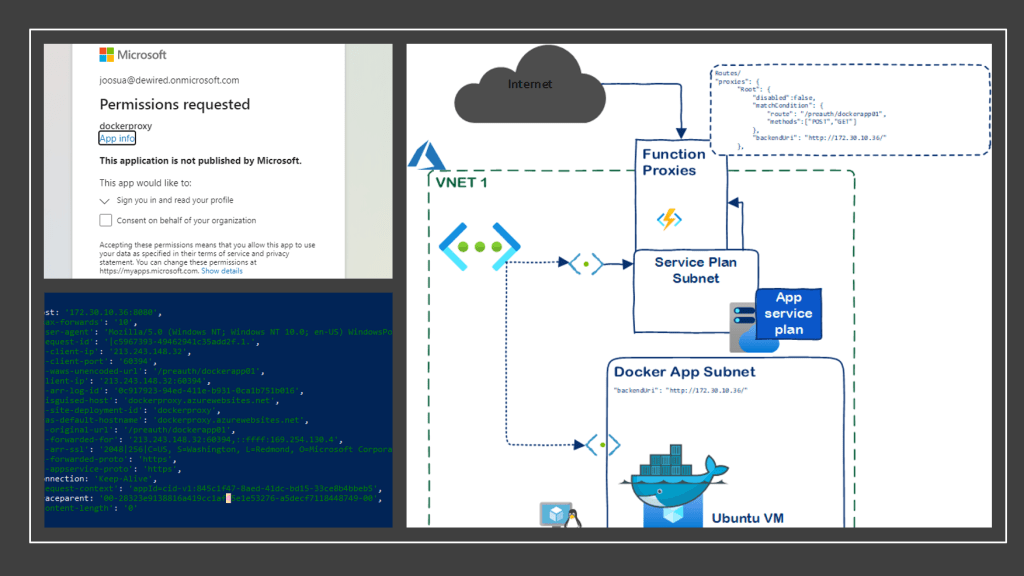
Disclaimer: Azure Function Proxies are meant to act as proxies for functions itself, and as aggregators of microservice style resources/API’sLue lisää
Background Many enterprise applications rely on group /role information to be passed on assertions for authorization, and further role decisions.Lue lisää
Remote connectivity and development environment https://code.visualstudio.com/docs/remote/ssh https://code.visualstudio.com/blogs/2020/03/02/docker-in-wsl2 https://docs.microsoft.com/en-us/azure/security-center/security-center-just-in-time Secrets management, container security in Azure and runtime security options https://securecloud.blog/2020/04/24/hidden-gem-in-azure-scan-your-docker-images-in-acr-view-results-in-sub-assessment-api-and-azure-security-center/ https://securecloud.blog/2020/04/15/nodejs-azure-key-vault-injecting-secrets-at-runtime-or-how-to-keep-code-clean-of-plaintext-secrets/Lue lisää
Azure AD Sentinel Workbook sweetness Background I am currently in the process of enriching logs for a bit larger project.Lue lisää