Why I consider this feature a true hidden gem? Well like many of my favorite Azure Services (Key Vault etc) these services are usable regardless of where you run the actual service. You might be running your docker container in private or public cloud. Regardless of the location images can be scanned by Azure Security Center, as long as you allow them to be pushed to the Azure Container Registry (Later ACR). Obviously I am biased to run those docker images in Azure, as I can choose per use case whether to use App Service, Linux VM’s or Kubernetes Cluster 🙂

Why use the Sub Assessment API?
I would consider Sub Assessment API an excellent compliment to an existing CI/CD platform. You can integrate results from the API as conditions to evaluate if there is need fix security vulnerabilities found in images before pushing anything further in the process.

Background
Before proceeding you might want to check MS’s excellent existing documentation on container security features
Image scanning
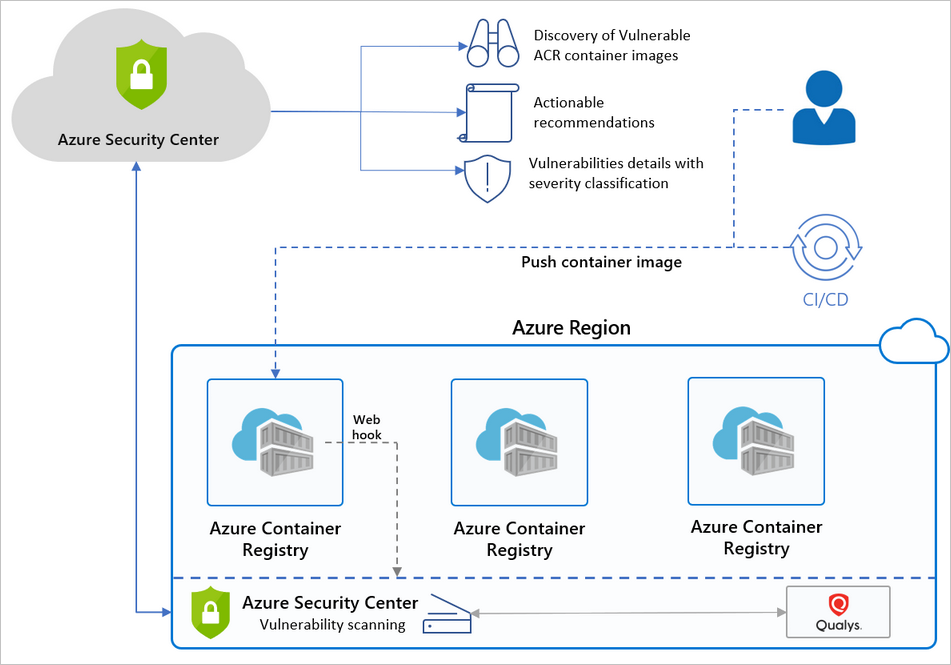
Docker host scanning
Continuous monitoring of Kubernetes clusters
Scan results for docker images in ACR
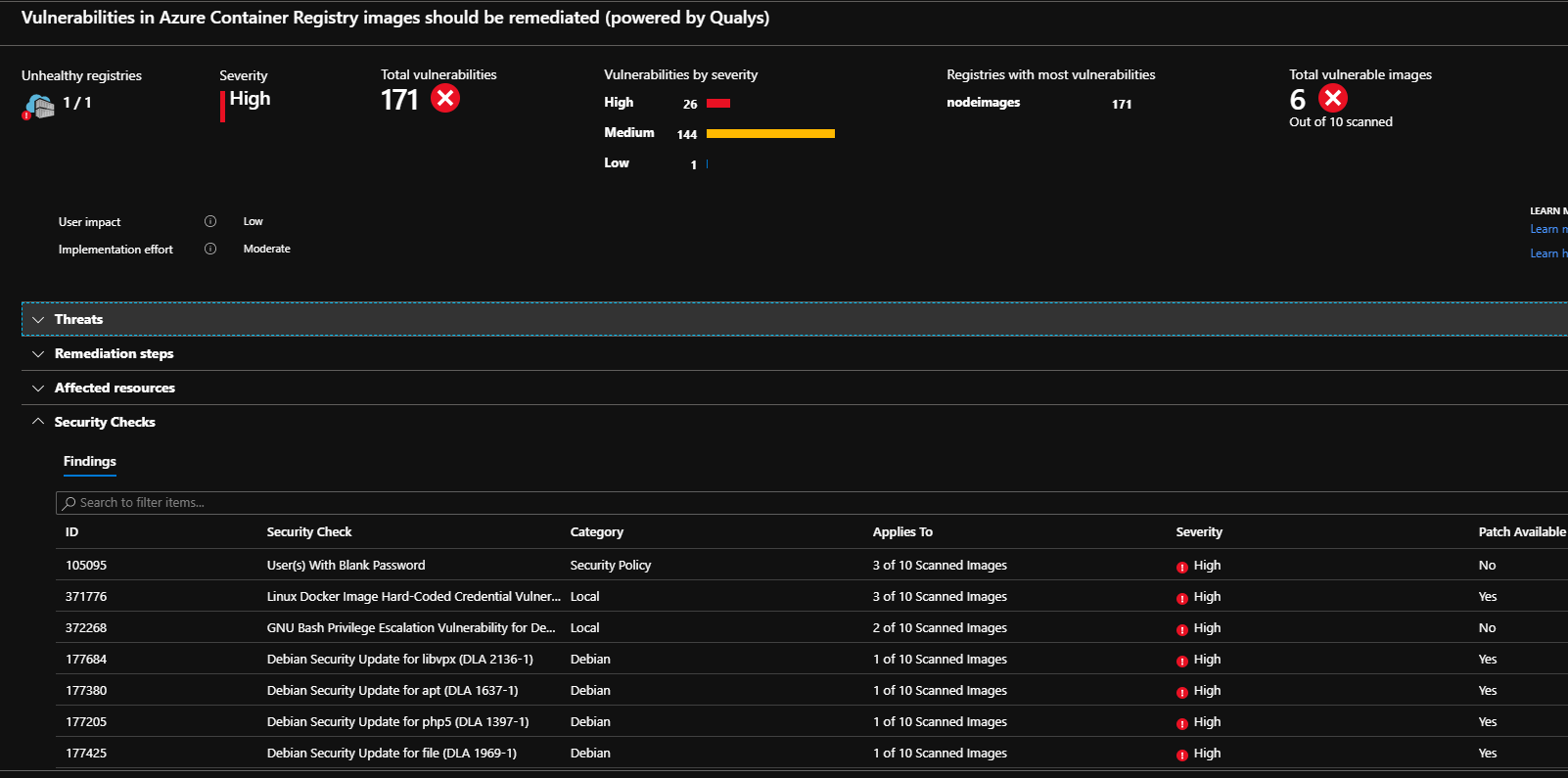
| Vulnerabilities in Azure Container Registry images should be remediated (powered by Qualys) | Container image vulnerability assessment scans your registry for security vulnerabilities on each pushed container image and exposes detailed findings per image. Resolving the vulnerabilities can greatly improve your containers’ security posture and protect them from attacks. (No related policy) |
Cost details
Security Center Standard https://docs.microsoft.com/en-us/azure/security-center/security-center-pricing
ACR https://azure.microsoft.com/en-us/services/container-registry
The per image cost is very reasonable (excluding other subscription enabled ASC costs you might have enabled)

What is done in this blog?
- Push set of images to ACR
- Via DevOps Pipeline to build and push images
- Via your local repository
- View scan results in Security Center
- View scan results via the assessments API
What are the recommended pre-requisites?
Note this is just my setup, but its pretty damn good for this use case.
If you are seasoned Linux Pro you might have something else, but for me WSL2 bridges many gaps, and is super easy to use 🙂
- WSL2 via the insiders preview (soon to be on the mainstream release)
- Docker Desktop using WSL2 back-end
- VSCode with Docker Extensions
I have the setup running as separate VM using Nested Virtualization. This keeps my main desktop fairly clean, and I don’t have Docker Desktop running in the background when I am doing something entirely non-related
The setup
Provision Azure Container Registry

If you are not using the Devops Pipeline option, then assign existing, or new Service Principal to the IAM settings as contributor (Service Principal is created as app registration in Azure AD App Registrations)

Pull any image you would like to scan from Docker Hub, or use your own image

Login to the image registry with AppID of the registry service principal

Tag your image locally in order to push it to the repository

Push the image the ACR

Alternatively you can build your own image in Azure Devops based on the application code stored in Repo, and use build pipeline to achieve similar result
Wait about 10 minutes to see the scan results in Security Center

Detailed results can be reviewed by clicking individual items

Using the Sub Assessment API
KB: https://docs.microsoft.com/en-us/rest/api/securitycenter/subassessments/listall
In my example I give access to all assessments under Microsoft.Security provider for the registry account. Typically you would give more narrow scope for the account:

Query the URI with Access Token using Client Credentials Flow
https://management.azure.com/subscriptions/{subscription}/providers/Microsoft.Security/subAssessments?api-version=2019-01-01-preview
Short script to filter High Severity results from the API
The script will show detailed data from the API, which you can for example integrate with your devops tool 🙂
Short example of the NodeJS script
var rq = require('request')
var util = require('util')
var options = {
client_id: "yourAppId",
client_secret:process.env[KeyVaultSecret],
resource:"https://management.azure.com",
}
var uri = "https://management.azure.com/subscriptions/6193053b-408b-44d0-b20f-4e29b9b67394/providers/Microsoft.Security/subAssessments?api-version=2019-01-01-preview"
function GetSubAssessment ({client_id,client_secret,resource},uri) {
return new Promise ((resolve,reject) => {
var options = {
json:true,
headers:[{
"content-type":"application/x-www-form-urlencoded"
}
],
form: {
grant_type:"client_credentials",
client_id,
client_secret,
resource,
}
}
rq.post("https://login.microsoftonline.com/dewired.onmicrosoft.com/oauth2/token",options, (error,response) => {
// console.log(response.body)
if (error) {return reject(response.body)}
//resolve(response.body)
var securityAPIoptions = {
json:true,
uri,
headers:{
"Authorization": "Bearer " + response.body.access_token
}
}
rq.get(securityAPIoptions,(error,response2) => {
var obj = response2.body.value
console.log(obj.length)
//filter high results
var results = obj.filter((status) => {
return status.properties.status.severity =="High"
})
resolve(results)
// return resolve("printed results")
})
}
)
})
}
GetSubAssessment(options,uri).then((data) => {
console.log(util.inspect(data,false,10,true))
}
)
The script will output results Selected in the filtering function :

Recommended further reading
https://docs.docker.com/docker-for-windows/wsl-tech-preview/
Br, Joosua





0 comments on “Hidden gem in Azure: Scan your docker images in ACR, view results in Sub Assessment API and Azure Security Center”