Background
Azure IpaaS * or Azure Integration services is set of services for creating rich integrations between often disparate systems.
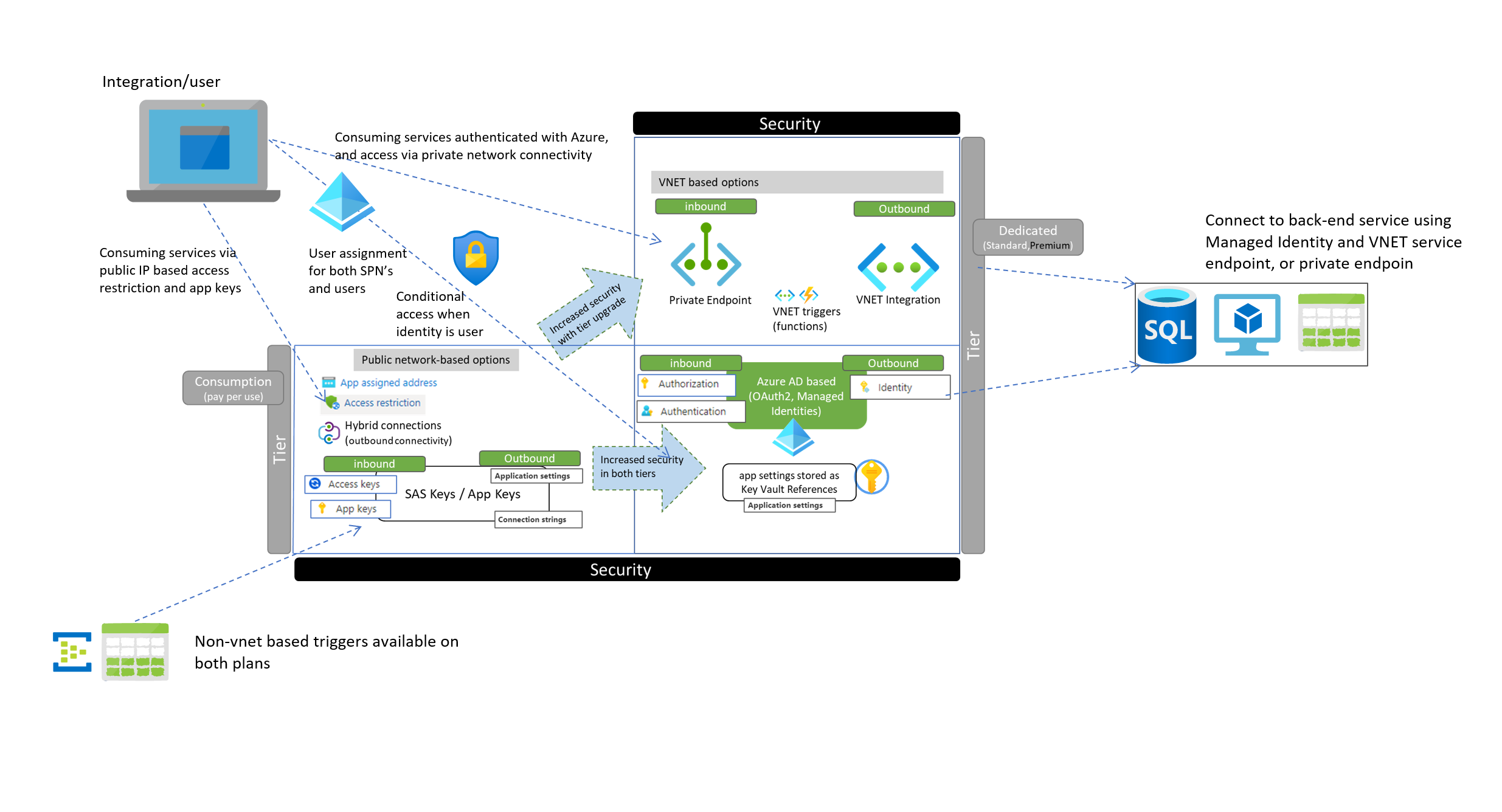
This blog focuses on security baseline regarding network and authn/z options for Logic Apps and Functions. For quality information regarding integration services I recommend the MS article below for exploring various integration areas

* Often associated with Azure Logic apps
Short example of scenarios
Scaling / Pricing etc
There are scaling and pricing differences/benefits on both models (consumption and non-consumption) which may influence selection of the plan type regardless of the security options presented here.

Authn/z options
- Both functions and logic apps offer
- inbound access for HTTP Triggers to be invoked via static key based credential (app keys and SAS keys for logic apps)
- Can use static keys in app settings (with or without Key Vault Integration) on outbound calls, or output bindings (functions) and connectors (Logic apps) calling SQL for example, or using storage output binding)
- Both functions and logic apps offer
- inbound access for HTTP Triggers to be authorized based on Oauth2 token of the caller
- Outbound access to downstream services based on Managed Identity of the service. This enables the downstream services to authorize the Function or Logic app based on the OAuth2 token
Generally the benefit of Oauth2 based authorization is, that the caller does not transmit long lived key in the request towards the endpoint, and Azure AD / RBAC has thus authority, whether the token is issued for the caller. With static keys Azure AD does not have such authority, as the authn/z is not based on Azure AD
Network options
The major distinction between consumption and dedicated (Premium / Standard) plans is VNET and Private Endpoint based options, for both inbound and outbound access. Consumption plan does not offer either, so it’s easy decision criteria if you need advanced VNET options
Scenarios with integration examples
Below are few examples regarding outbound and inbound access for integrations
References
Below is list of references on this blog
https://docs.microsoft.com/en-us/azure/azure-functions/
https://docs.microsoft.com/en-us/azure/logic-apps/
Deep-diver: Hardening authentication and authorization between logic apps and API management
Azure API Management – Call Azure Functions with Managed Identity
App Service – Key Vault Vnet Service Endpoint access options explored + NodeJS runtime examples
Deep diver – NodeJS with Azure Web apps and Azure Blob Storage SAS Authorization options

0 comments on “Azure Integration baseline security: Network and authentication and authorization”