Background
I recently wrote about top-3 benefits of Azure Security Center, one of the benefits was advanced alerting which is true hidden gem. I’ve decided to gather some exhibits of such events into this short blog series. As with this exhibit its clear that Azure Security Center is well suited for securing PaaS workloads in Azure, which is the topic covered in this blog
Before proceeding, be sure to check the long list of alerts made available by Azure Security Center Standard alerts list at docsmsft.

Detecting SQLI
What is SQLI?
In short SQLI can be described as malicious code thats ”smugled” as part of often un-sanitized user input, via many of the available user input methods found in typical website
- There is good description also available at docs@msft

Whats needed?

- Detecting SQL injection, and many data security options are available via the Advanced Data Security which is part of Azure Security Center Standard. The feature we are testing here is Advanced Threat Protection
Exhibits (What happens when such event occurs)
SQL.DB_PotentialSqlInjection
I am currently testing Azure Logic Apps as possible attack vector, and how to detect such attacks with Advanced Threat Protection in Azure Security Center

- Below is example of the very simple SQLI from un-sanitized user input that gets translated to SQL query, which I am passing from my NodeJS app.

- Its translated into SQL query action in Azure Logic Apps

Alerting
- In this case the culprit was me once again (surprise surprise…)
- Teams alert arrived upon the attempt of SQLI

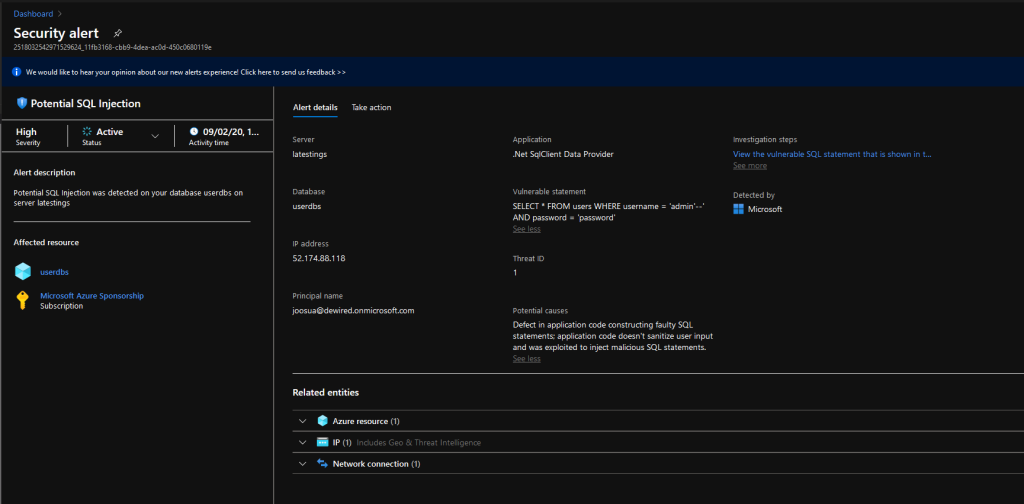
- If we select Triage, we can see the whole event in Azure Security Center with causes and all
Potential causes Defect in application code constructing faulty SQL statements; application code doesn't sanitize user input and was exploited to inject malicious SQL statements. Vulnerable statement SELECT * FROM users WHERE username = 'admin'--' AND password = 'password'
References
Till next time!
0 comments on “Azure Security Center Exhibits from the field – Detecting SQL Injection with Advanced Data Security”