One of the coolest services for MSP’s and ISV’s for building and running services on Azure in unified manner and scale is definitely Azure Lighthouse – This blog details an way to increase security of Azure Lighthouse use for both customers and MSP’s
update 4.2.2021
- Updated MFA auditing
Reasoning
If you allow delegated management of your Azure Services by 3rd parties, its recommended to ensure that these 3rd parties have some good security measures in place to avoid misuse of privileged access.
*3rd party in this context in the rest of the blog is referred as MSP (Managed Service Provider) or ISV (Independent Software Vendor)
Target audience
This guide is meant for both MSP and Customer to implement together. As customers can’t force the use of PIM for direct delegation of Azure Resources (non B2B delegation) – if you want to generally know more about cross-tenant management including Azure Lighthouse, I recommend to take look at this excellent article
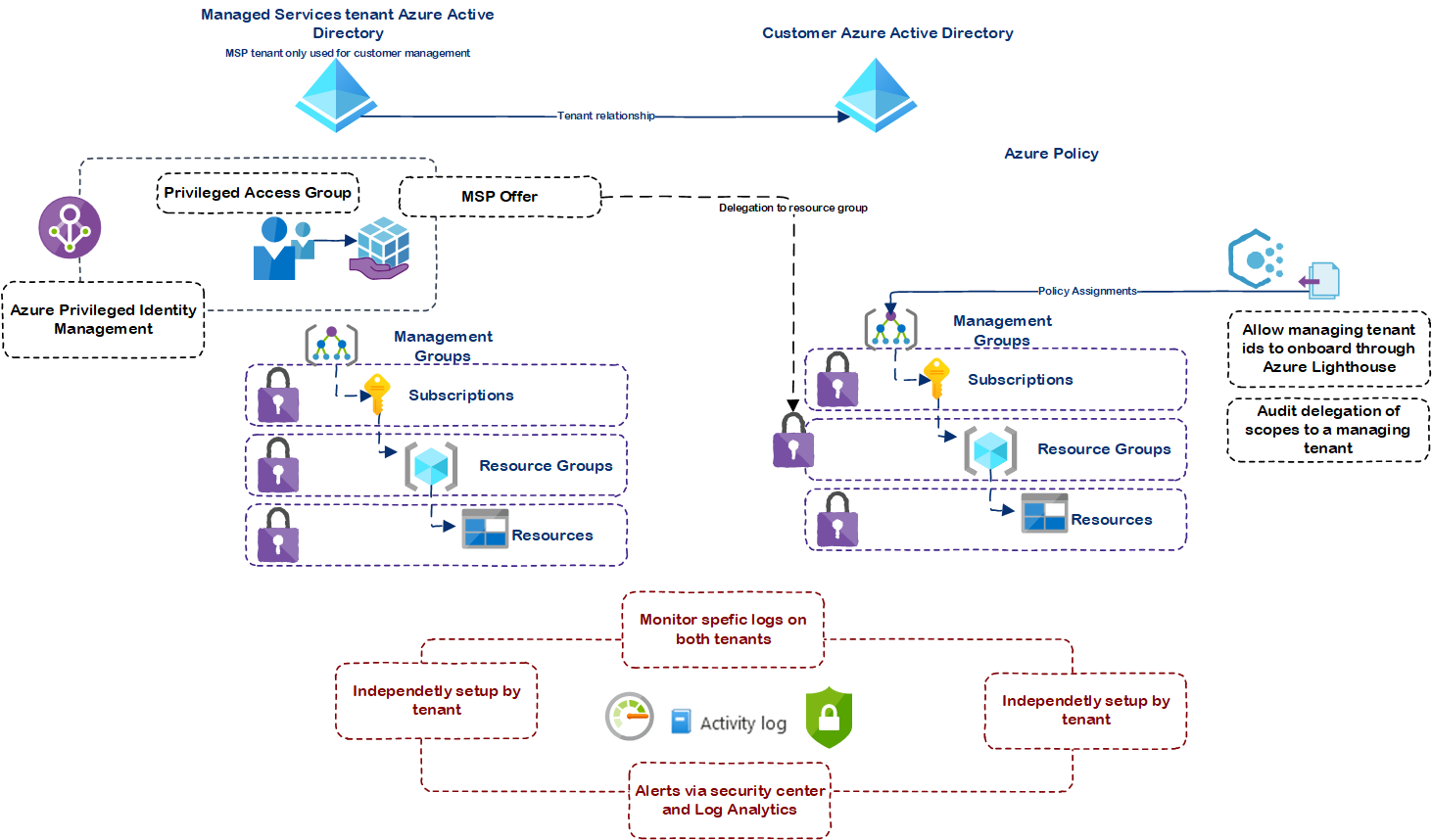
One of the best ways to secure any administrative Azure use is removing permanent delegated access from MSP side user accounts to customer tenants – And as always auditing via Azure Monitor, and Azure Policy will provide insights into compliance, and restrict which MSP’s can be enabled for delegated resource management in the first place.
Benefits
No standing access
No permanent access is enabled for the MSP side customer admins, rather per session based temporary elevation of privilege per customer environment
Enhanced access auditing in MSP side
In terms of overall auditing, the PIM activation of per customer dedicated Privileged Access Group Provides an single audited gate, which produces audit log also on activation on accessing customer resources (customer side receives the normal Azure Activity log, which is not ”PIM aware”)

Enable customer to receive notifications when access to their environment is activated via Azure lighthouse

Actions to be completed
- Removing permanent access can be done by allowing only temporary access to the delegated management to Azure Lighthouse via Azure AD Privileged Identity management.
- Auditing MSP’s delegated actions, and restricting which tenants can in the first place be granted delegated access is achieved with this MS Docs guide
| Scenario | Customer | Service Provider | Service |
|---|---|---|---|
| Require delegation of access to be controlled by Azure Active Privileged Identity Management (link) | This setting is not controlled by customer | This setting is achieved by use PIM and Privileged Access Groups in Azure AD | Azure Privileged Identity Management |
| Restrict access to pre-approved MSP’s (link) | This setting is controlled by the customer tenant, by the use of Azure Policy ’Allow managing tenant ids to onboard through Azure Lighthouse’ | This setting is not controlled by MSP | Azure Policy |
| Audit delegations (link) | This setting is controlled by the customer tenant, by the use of Azure Policy ’Audit delegation of scopes to a managing tenant’ and the ’Service Providers view’ in Azure Portal | This setting is not controlled by MSP | Azure Policy |
| Audit operations in Activity log (link) | This can be achieved in both tenants | This can be achieved in both tenants | Azure Monitor |
| Enable customer to receive notifications when access to their environment is activated (link) (Optional, but recommended as customers will receive better visibility for administration performed based on delegated access) | This setting is not controlled by customer | This setting is achieved by use PIM and notification settings | Azure Privileged Identity Management |

List of related principles from Azure Security Benchmark
These are principles that should be followed on any Azure environments, but in this context this is focused on the MSP having access to customer environments via Azure LightHouse Delegation
| Use dedicated administrative accounts | Azure Security Benchmark (v1) |
| Log and alert on suspicious activities from administrative accounts | Azure Security Benchmark (v1) |
| Regularly review and reconcile user access | Azure Security Benchmark (v1) |
| Monitor attempts to access deactivated credentials | Azure Security Benchmark (v1) |
Require access to delegation to be controlled by Azure Active Privileged Identity Management
Background
This feature is possible by using new feature called Privileged access groups in Azure Privileged Identity Management.
TLDR version: is that you can control group member and ownership via PIM, just like you would control any other member for PIM activated role

Require delegation of access to be controlled by Azure Active Privileged Identity Management
- Create the group you plan to use for delegation in the service providers tenant
- For Group Naming Convention I like the term PAG ’Privileged Access Groups’, presumably coined by ’Thomas Naunheim’

- Once the group is created enable it for ’Privileged Access’ in group settings

- Add the admins who are supposed to operate the customer environment via Azure Lighthouse

- Require MFA to be verified on activation of the member role

Example from Azure Lighthouse deployment parameters file

{
"$schema": "https://schema.management.azure.com/schemas/2015-01-01/deploymentParameters.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"mspOfferName": {
"value": "SecureCloudBlog Api management by delegation from MSP"
},
"rgName": {
"value": "RG-APIM"
},
"mspOfferDescription": {
"value": "SecureCloudBlog Api management by delegation from MSP"
},
"managedByTenantId": {
"value": "46d2c4e6-a732-4fb4-b9f8-374af03f3f58"
},
"authorizations": {
"value": [
{
"principalId": "e4b96ec3-6c96-4279-85a8-1441253cd6a7",
"principalIdDisplayName": "PAG - AzLightHouse - Customer SecureCloudBlog provider",
"roleDefinitionId": "b24988ac-6180-42a0-ab88-20f7382dd24c"
}
]
}
}
}
Example access as authorized user
- No delegations when signed in are visible (as expected)

- Activate the PAG access



- Upon activation the MSP admin will see the delegated access available in the subscriptions filter

Enable customer to receive notifications when access to their environment is activated via Azure lighthouse


Sometimes it might be beneficial to notify the customer on access activation, as the customer side audit log does mostly log data plane access attempts, and actions logged generally by Azure Activity Log
Audit delegations in Azure Lighthouse
There is two ways to review and audit delegations set by service providers
- Service provider view in Azure Portal
- This view is very useful and detailed view, and would be the first place start reviewing delegations from service providers

2. Azure Policy (Supposed to show non-compliant for all delegations)

Allow managing tenant ids to onboard through Azure Lighthouse


- List of tenants are are supposed to match the ones you initially want to be allowed service providers




Audit operations in Activity log
Administrative operations captured by Activity Logs can be used to audit delegated access. Perhaps there will be another blog, on how to audit these logs from Log Analytics side, to create new correlations and alerts

How to audit MFA use without sign-in logs for Azure Lighthouse based access?
You can confirm if MFA was used by the partner from activity logs by inspecting the claims



References
https://docs.microsoft.com/en-us/azure/lighthouse/concepts/cross-tenant-management-experience
https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-configure
https://docs.microsoft.com/en-us/azure/security/benchmarks/introduction

Paluuviite: MSPs Access to Azure Sentinel and M365 Defender – Sam's Corner