
Often when I hear Single Logout (or SLO) I tend to think about SAML2’s SLO feature. Recently Azure AD OAuth2 logout implementation crept up on me, and I couldn’t say for sure how well it aligns with SAML2 SLO – So to find out I did bit of exploration and documented my findings here:
SAML Single Logout/Sign-out

- The main function of the feature with Azure AD implementation is to ensure that Azure AD will send a sign-out request to all applications user has signed in during the same browser session.
- When properly implemented Azure AD will send logout request to the URL defined within app registrations Logout URL setting, delivered in iframe within the browser the session was established from
- by proper implementation, it means that the application has to clear session persistence references from itself. There are many ways to do this, so I won’t delve in to details, but in general it might be clearing the users cookies, and marking session settings in the back-end too.
- Its good to know, that there are some scenarios where single logout has to work in order to satisfy the legal requirements of certain apps
Testing SLO for OAuth2
My first step was to set the App Registrations logout URL to match my own logout endpoint. Next I logged in to my application, and browsed to Office 365 see what Azure AD does when user initiates the logout from Office365 or Azure Portal (And not from the app itself)
SID parameter?
- Upon the logout I saw only single parameter, ”SID”, which led me to believe that it was the user’s SID. It turns it wasn’t, and after some Googling, I came about StackOverFlow question with excellent answer, which sheds some light to the SID attribute (query param), which in hindsight makes perfect sense.
- Stackoverflow credits to @JoonasWestlin

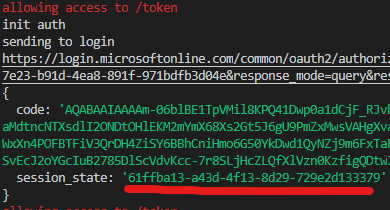
Session_state

- Session state is attribute delivered with authorization code, as additional parameter.
- Its up to the developer to decide on how to store the value to be referenced later with the SLO request (cookies, session store, back-end etc)
- When the logout request is ”broadcasted” from Azure AD, it sends this value to the logout URL defined in the app registration
- The session_state matches the SID value, which you captured in earlier state
High level flow example
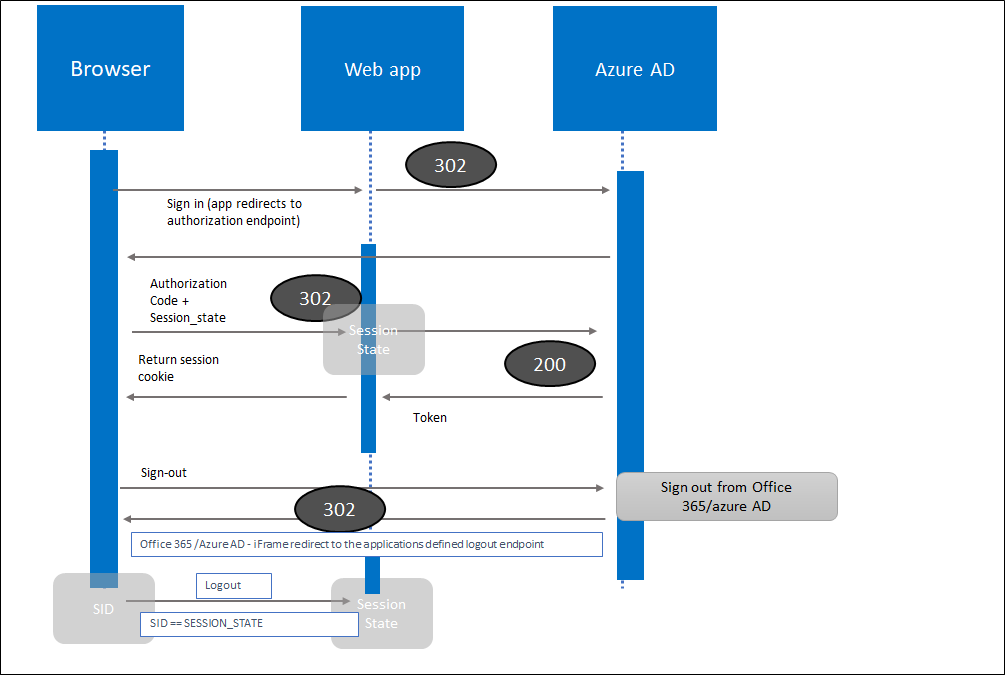
- The authorization code serves as example of showing where the session_state param is delivered (if you want full depiction of authorization code flow check this article)
- In the last part iframe sends the logout request to the web app via redirect, and app clears cookies, and marks the session to end in the back-end


References
Till next time!
Br, Joosua



Hi Joosua, I really like this article regarding the Single Logout.
Althought, I cannot figure out the implementation.
Is there any chance you could share a simple HTML file showing how you capturing the LogOut URL callback from Azure?
I have 3 application that share the same tenant, but I cannot get the Single Logout to work. The user needs to logout from each of the SSO application it navigated previously.
Also, great article on B2X: https://securecloud.blog/2020/06/08/azure-ad-b2x-is-here-yes-b2x-not-b2c-or-b2b-debugging-and-insights/
Any help would be much appreciated.
Thanks,
Francisco
TykkääTykkää
Hi, I am currently on mobile, but once reach back to my desktop, I will try answer in detail, in case I have solutions for your questions. The slo is query parameter, which I have defined on my NodeJS to be listened in particular route (/slo) – html would be clientside part only, and you can peek how ms sends the query parameter on iFrame to be received on the server side – thx for the feedback!
TykkääTykkää
Hi Joosua, I’ve tried to work on the iframe call from Azure B2C and I came across an issue with Chrome and SameSite cookie, but even on MS Edge I am not able to get the GET Method made to LogoutURL. If you send me an email, I could reply with my 2 Javascript application that I am trying to accomplish on Single Sign-Out.
Do I need to do anything with the Session_State parameter that Azure submits on the reply after login? And because I cannot see the iframe call, I cannot also get/understand the ”sid” parameter on the logout process.
Another different that I see, is that for authority I am using my Azure B2C tenant:
const _tenant = ”https://{tenant}.b2clogin.com/{tenant}.onmicrosoft.com/”;
instead of :
authority: ”https://login.microsoftonline.com/common”
Thanks,
TykkääTykkää
Hi, I can try an spin-up Azure AD version. It might also be related to the Azure AD B2C, more than AAD, for which this worked ok – my email is joosua.santasalo@outlook.com
TykkääTykkää